Malware Analysis Process Essay
Malware Process Analysis Essay
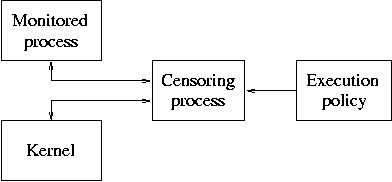
When you upload a malicious file, this application can return basic file information (hashes, name, type, etc. Part I: Unpacking, Hooking, and Process Injection; Part II: Analysis of the core IcedID Payload (Parent process) Part III: Analysis of the child processes; This blog is Part I below. A process can create another process by running a specific computer instruction and specifying an executable file (.exe) to launch.. I still do not know a lot about this topic, but I …. In static analysis, the disassembly code files are analyzed for the malicious system calls. The analysis of the malware can be performed by using the sandboxes and monitoring the process of malware. A model is to be built for the control flow graphs Jun 10, 2017 · Welcome to a two, maybe three part series that going to teach you the basics of Dynamic Malware Analysis. The thoroughness of the tool is also weakness, as the amount of data captured by Process Monitor can easily overwhelm the analyst Nov 25, 2012 · Analyzing Malware• Runtime / Dynamic Analysis Pada tahapan ini seorang malware analyst mencoba mengeksekusi malware tersebut untuk melihat behavior dari malware tersebut. The latest version of Process Explorer can be downloaded here.. My Assignment Help for CTEC5807 Malware Analysis Assignment Help. Dissertation Methodology Writers Site Au
Creative Writing Course Manchester University
We use holistic process to dismantle the malware technology so that we can determine the function and purpose of the. The entire detailed analysis is divided into three parts. Virtualization software[9] such as VMWare, Virtual Box provides options to create such an environment. This time, it was not an exercise! This will mainly be guidance based on …. Breaking Threat Analysis research paper by FortiGuard Labs . The behavioral analysis tool has to identify the nature of the tool and the behavior of malware. The genesis of computer viruses started in early 1980 when some researchers came up with self-replicating computer programs. A variety of tools and techniques need to be employed to ensure that the underlying information is revealed. Security incident responders benefit from knowing how to reverse-engineer malware, because this process helps in. Ethical Hacking: The Complete Malware Analysis Process Course Intermediate Start my 1-month free trial Now let's get started learning complete malware analysis A very important use case for malware analysts is long-term malware analysis. Jul 09, 2019 · Malware analysis tools and techniques. Apr 25, 2019 · Malware analysis is of utmost importance since it helps understand malware infections and stop malware from spreading into other systems, files, directories etc. It creates a new process // and its primary thread.
Writing Helper Wordpress Plugin
Sample Resume For Intermediate Students – In Practical Malware Analysis, Chapter 3. Aug 27, 2011 · Process Monitor is a free tool from Microsoft that displays file system, registry, process, and other activities on the system. As an example, also explore the construction of …. introducing Malware Analysis 2. Whether you are wanting to analyze potentially malicious files manually or unleash the full power of SOAR, we now offer an application on Apphub to automate your malware analysis process. Collection and analysis of cyber threats in QATAR to determine the effect of such threats to the nation. It demonstrates the cyber attack lifecycle from the initial exploit and malware execution path to call back destinations and follow on binary download attempts If you fail to decrypt the desired file, document the process with a file of your choice (where you know the key) for half the points of this item. Analysis is a process of inspecting samples of a piece of malware to find out more about its nature, functionality and purpose. Malware analysis may seem like a daunting task for the non-technical user. justify structural inequality….

This will mainly be guidance based on …. Use a combination of static and dynamic analysis tools and techniques discussed throughout the course. I started digging into “malware analysis” some time ago, mostly because I did not know anything about malware (except that they were not nice). STATIC ANALYSIS. Any program that is intended to disrupt computer or network operation, gather sensitive information, gain access to private computer systems or networks is malware. Oct 11, 2010 · Behavioral analysis examines the malware specimen's interactions with its environment: the file system, the registry (if on Windows), the network, as well as other processes and OS components. Part I: Unpacking, Hooking, and Process Injection; Part II: Analysis of the core IcedID Payload (Parent process) Part III: Analysis of the child processes; This blog is Part I below. The response in the case of a malware attack has several main phases: preparation, detecting and analyzing the attack, containing, eradicating and recovering from the attack, and activities after the attack. Working with U.S. First, the malware starts a legitimate process using CreateProcess using the CREATE_SUSPENDED option in the fdwCreate flags parameter. It’s an invaluable tool for troubleshooting Windows problems as well as for malware forensics and analysis tasks. These may come …. Stages of malware analysis are layered on top of each other, forming a pyramid with an upward complexity. Static. Static malware analysis or code analysis is the process of analysing malware by inspecting the source code or the binary files of the malware without executing malware [2].
